TL;DR:
There's so much to security especially around the perimeter with various entry points into infrastructure and our applications
SSO, IAM, and RBAC granularize the approach to defense-in-depth ensuring streamlined authentication and authorization
OpenUnison simplifies the SSO process, MyVirtualDirectory aggregates multiple identity sources, Kubernetes authentication magic thanks to Tremolo Security
In the rapidly advancing digital era, businesses are transitioning from traditional on-premises IT infrastructures to cloud-native environments to enhance agility, scalability, and efficiency. However, this shift also brings about a significant transformation in the security landscape. In this blog, we will explore the security challenges that traditionally existed and how they are being addressed in the cloud-native paradigm.
Let’s rewind a couple of years. We were running all physical hardware, and we had physical access to almost everything that ran our business. There weren’t the overly complicated concepts of cloud and distributed environments. Everyone who needed to do anything always did it in person from offices.
Fast forward to the present day, and everyone prefers the cloud over owning all their physical servers, even if you’ve got physical servers, you have to deal with the problems you’d face on the cloud. Distributed computing has become a widespread adoption, folks are working from all over the world and from different timezones.
All these changes, in various domains, have also introduced many security risks, and have forced us to rethink how we do security. Let’s take a look at some of the technicalities of what security systems used to be like, and how they’ve evolved for modern-day problems
Perimeter Security Model
In a much more traditional era, organizations relied on a perimeter defence model, envisioning their networks as castles surrounded by moats. This model assumed that all entities within the internal network were trustworthy, granting unrestricted access. However, this approach had significant limitations:
Lack of Granular Control: Perimeter security assumed every device within the network was trusted, lacking granular control. This vulnerability exposed organizations to threats like credential leaks, human errors, insider attacks, and infected devices.
Globalization and Remote Work: As a response to the shortcomings of the perimeter security model, Zero Trust Security emerged as a revolutionary paradigm. This approach challenges the default trust placed in internal networks, requiring continuous verification before granting access.

Image credits: istockphoto
Understand Zero Trust Security
Now, let’s understand what exactly is Zero Trust in a game-based scenario.
Imagine the digital world is like a big, bustling city, and everyone needs a special ID to get in. Now, enter our superhero, Zero Trust Security – the guardian of this city. Our hero has three special tasks to perform
Identity Verification: Just like showing your ID at the city gate, Zero Trust makes sure everyone entering is who they say they are. It's like meeting new friends and making sure they're cool before inviting them to play in the city.
Least Privilege Access: Think of this as giving keys to different rooms in your favourite game. Zero Trust makes sure everyone has the right keys for the tasks they need to do. No unnecessary keys – just like having access to the parts of the game you need to win.
Assume Breach: Picture a castle with secret passages and guards. Zero Trust acts like those guards, dividing the city into safe zones. Even if a mischievous character sneaks in, they can't go far. It's like having secret codes to protect the city from anything mischievous.
Now, our superhero Zero Trust has decided to visit a special place called Kubernetes – like a playground for all digital games. Here, Zero Trust uses special tools, just like magical powers, to keep everything safe. It's like having a superhero team for each game, making sure no one cheats or plays unfairly.
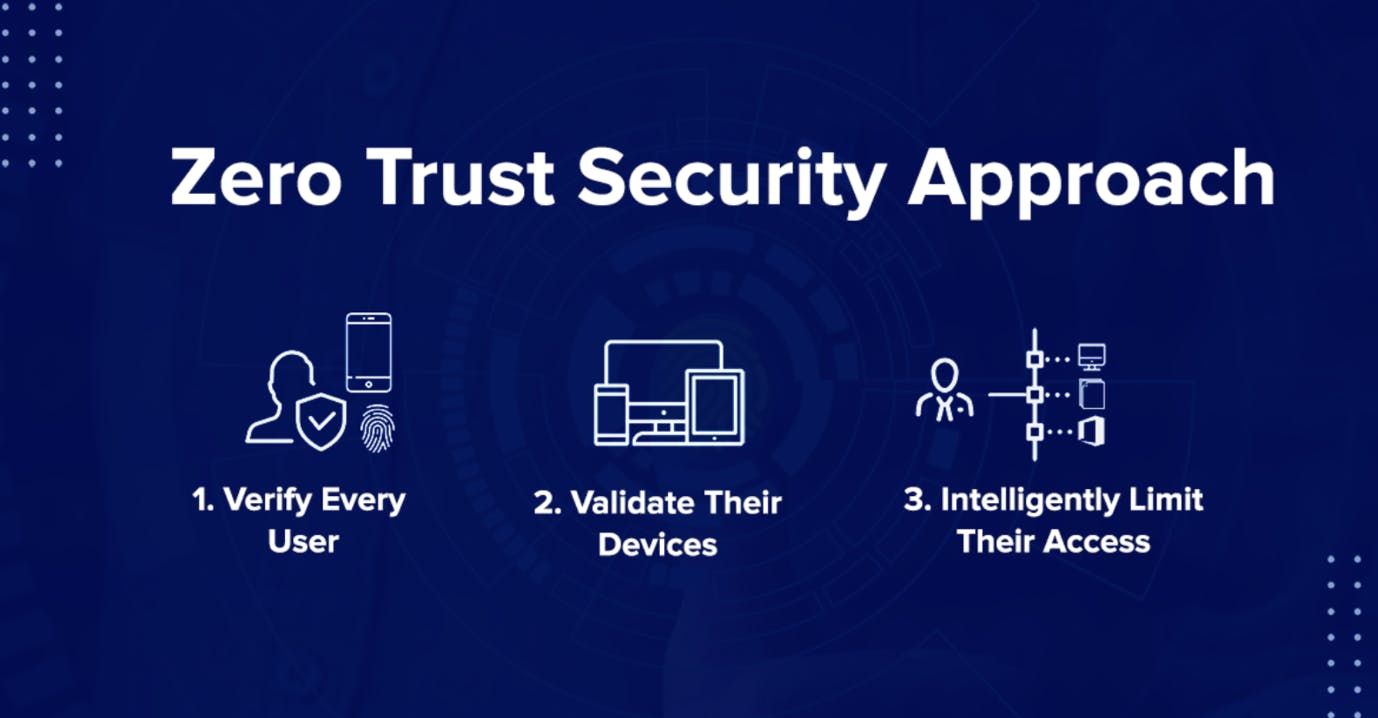
Image credits: quick launch
So, you see, Zero Trust is like the coolest superhero, making sure our digital city and playgrounds are always safe and fun. It's like having a friend who watches out for us in the big, exciting world of computers and internet adventures.
So, in the modern world Zero Trust offers these benefits:
Enhanced Security:
- Zero Trust reduces the attack surface, enables faster threat detection, and minimizes the impact of breaches through continuous verification.
Improved User Experience
- Zero Trust simplifies user access across different devices and locations, enhancing productivity and satisfaction.
Increased Agility and Innovation
- By providing a flexible and scalable security framework, Zero Trust supports digital transformation, cloud migration, and the adoption of new technologies without compromising security.
In conclusion, Zero Trust Security represents a paradigm shift from the traditional castle-and-moat approach, offering enhanced security, improved user experience, and increased agility in the dynamic landscape of modern networks and Kubernetes environments.
Different security models help secure your infrastructure and prevent malicious actors from gaining access. Let’s talk about some of those.
Single Sign On (SSO)
In the dynamic realm of the internet, where users navigate an ever-expanding array of websites and services, the demand for seamless authentication has never been higher. Single sign-on is the answer!
What is SSO Authentication?
SSO is the key to unlocking effortless logins across multiple domains. It tackles the challenge posed by the same-origin policy, offering a solution to share session information securely.
How SSO Works
Centralized Token Generation
A central domain creates a secure token (e.g., JSON Web Token).
This token becomes the golden key for user authentication across various domains.
Seamless User Authentication
Users logged in at one domain are automatically recognized and authenticated at others.
Overcomes the limitations of sharing session data imposed by browser policies.
Scenario without SSO – Juggling Multiple Credentials
Picture yourself working in a dynamic company that relies on various applications for daily operations. Each application, from email to project management and document collaboration, has its own login credentials. You find yourself juggling usernames and passwords throughout the day. This process not only slows you down but also leads to occasional password resets and the constant fear of forgetting one of the numerous credentials.
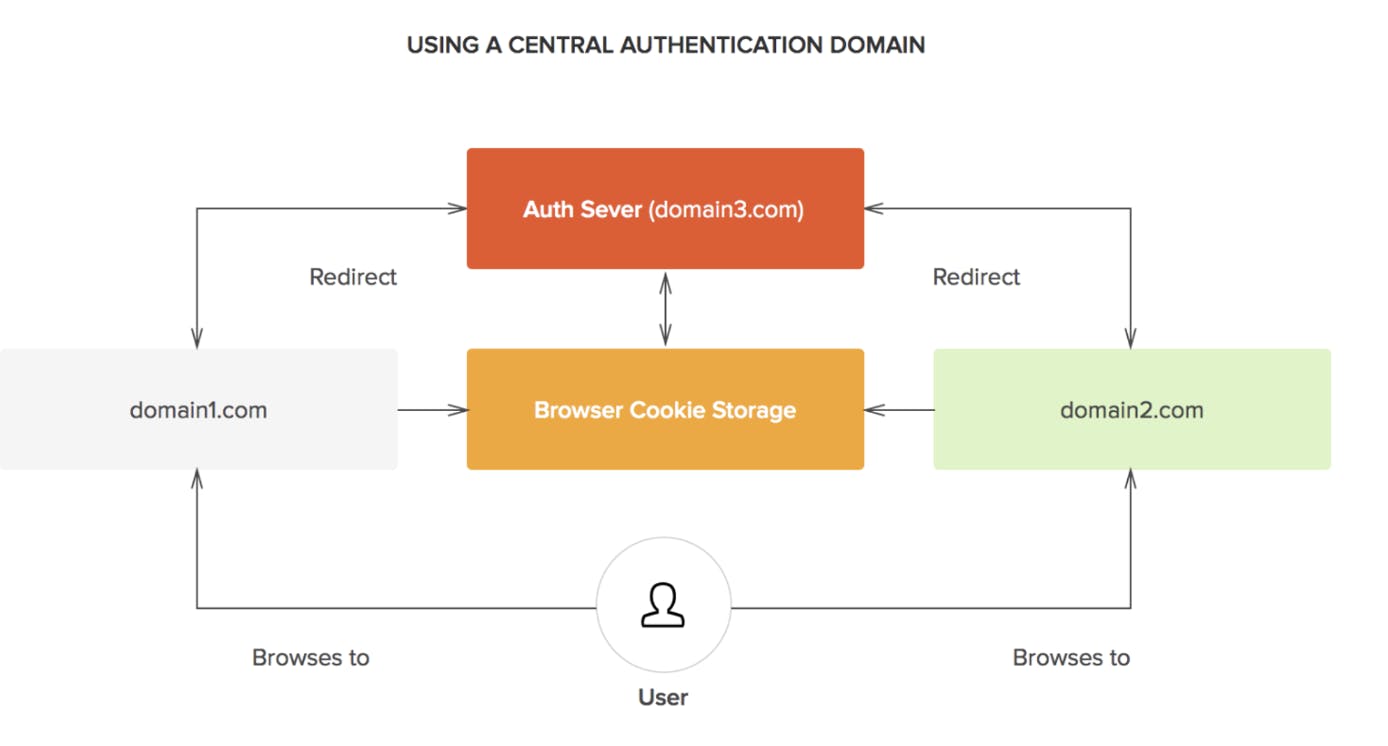
Image credit: auth0
Enter Single Sign-On : Streamlining Access
Now, the company has decided to implement Single Sign-On (SSO). It's like upgrading from a ring of separate keys for every door to a single master key. With SSO, you log in once, and it serves as your access pass to all the applications you need. No more juggling credentials, no more forgotten passwords. It's a seamless transition into your daily tasks without the friction of repetitive logins.
Benefits Unveiled
Enhanced User Experience
- Your workday becomes a breeze as you log in once, and all applications recognize you. No more navigating through different login screens, making the overall experience smoother and more enjoyable.
Centralized Security
- Previously, managing multiple credentials meant an increased risk of security breaches. With SSO, the security focus shifts to safeguarding that single entry point, enhancing overall security and reducing the risk associated with managing multiple sets of credentials.
Simplified User Management
- From an administrative standpoint, onboarding and offboarding employees become more straightforward. Access is granted or revoked centrally, eliminating the need to update credentials across various platforms. This centralized approach ensures a more organized and efficient user management process.
In this scenario, the adoption of Single Sign-On transforms a cumbersome and less secure environment into a streamlined, secure, and user-friendly digital workspace.
IAM: Safeguarding the Digital Gateway:
IAM is more than just a set of policies and technologies—it's a robust framework designed to manage and control user identities and access privileges effectively. By serving as the gatekeeper to organizational resources, IAM establishes a foundation for information security, offering secure and controlled access to systems, applications, data, and even physical facilities.
Key Components of IAM:
Identity Management:
Efficiently administers user identities, from provisioning to de-provisioning.
Mitigates security and compliance risks by ensuring accurate user data.
Authentication:
Verifies user identities through methods like passwords, multi-factor authentication, and biometrics.
Enforces password policies to enhance security.
Authorization:
Dictates access privileges based on roles, permissions, and policies.
Utilizes Role-Based Access Control (RBAC) models for efficient authorization management.
Single Sign-On (SSO):
Enhances user experience by allowing access to multiple applications with a single set of credentials.
Streamlines the login process and reduces the burden of managing multiple passwords.
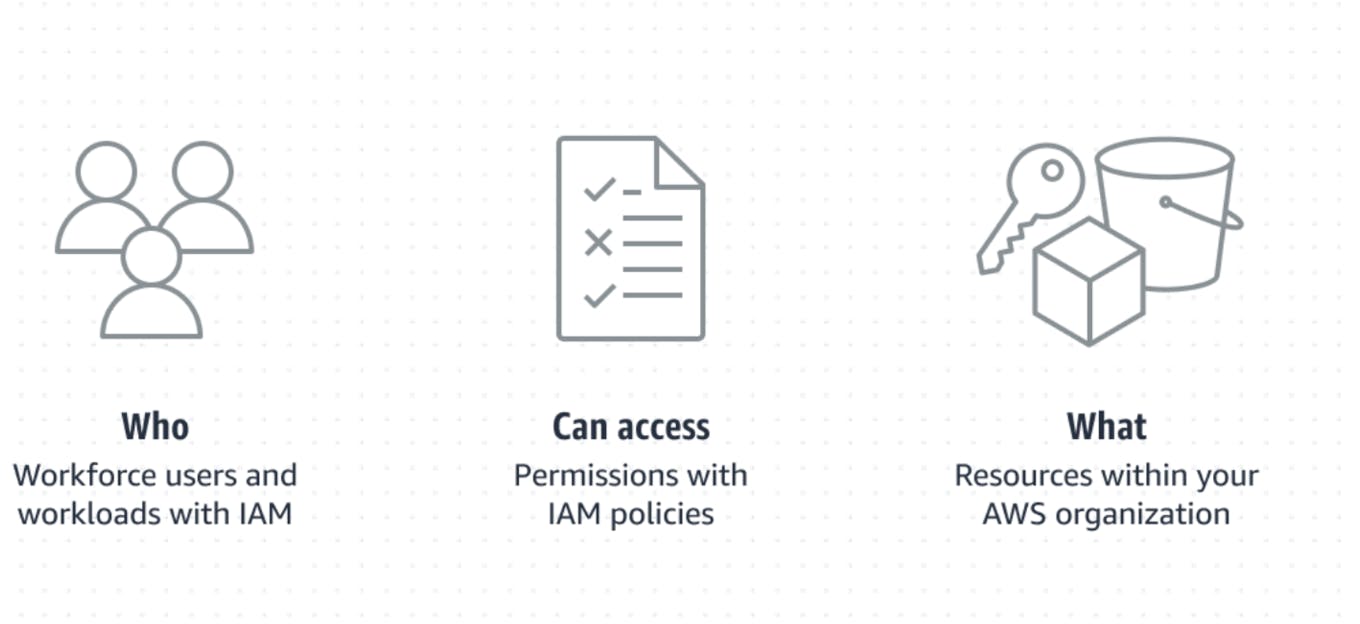
Image credits: AWS
Benefits of IAM Implementation:
Rock-Solid Security Shield:
- Imagine IAM as an impregnable fortress, keeping out unwanted guests and securing your data. It ensures your sensitive information stays safe, preserving its integrity, confidentiality, and constant availability.
Compliance Made Easy:
- IAM acts like a trusty guide in the maze of regulations. It ensures you follow data protection rules with ease, making audits a breeze and compliance reporting a smooth operation.
Effortless User Access Control:
- Think of IAM as a conductor leading an orchestra of user access. It simplifies managing identities, reducing the admin workload. IAM's coordination ensures smooth account setups, streamlined access, and automated user processes.
Boosting Productivity:
- IAM is the key to a more productive work environment. With features like Single Sign-On, forget the hassle of multiple passwords. It frees up time and energy, allowing users to focus on what matters.
Challenges in IAM Implementation:
While identity management does have its advantages, and security benefits, it’s not without its challenges. Let’s quickly get an overview of some of the challenges that are introduced with IAM.
Identity Lifecycle Management:
Crucial for managing the entire lifecycle of user identities.
Minimizes inaccuracies in user data to reduce security and compliance risks.
Authentication Security Concerns:
Ongoing challenges in maintaining secure authentication methods.
Emphasis on robust measures like multi-factor authentication.
Integration Hurdles:
Seamless integration with existing systems poses challenges.
Careful planning and adaptable IAM solutions are crucial for overcoming integration hurdles.
IAM is not just a tool; it's a dynamic landscape offering solutions that adapt to modern cybersecurity challenges. Successful implementation establishes a robust framework, ensuring secure, efficient, and scalable digital environments. IAM remains a critical component for access control, risk mitigation, and protection of valuable digital assets.
RBAC (Role-based Access Control )
Let’s try to understand RBAC in the form of a story.
Imagine you work in a bustling office building with multiple floors, each floor hosting different departments and sensitive information. Now, let's say your office decides to implement a system to control and monitor access, ensuring that employees can only enter areas relevant to their roles. This system is the real-world equivalent of Role-Based Access Control (RBAC).
Picture yourself as an employee – let's call you Alex. You have a specific role in the company, and you only need access to certain floors and departments to do your job effectively. This is where RBAC steps in as the office security guard.
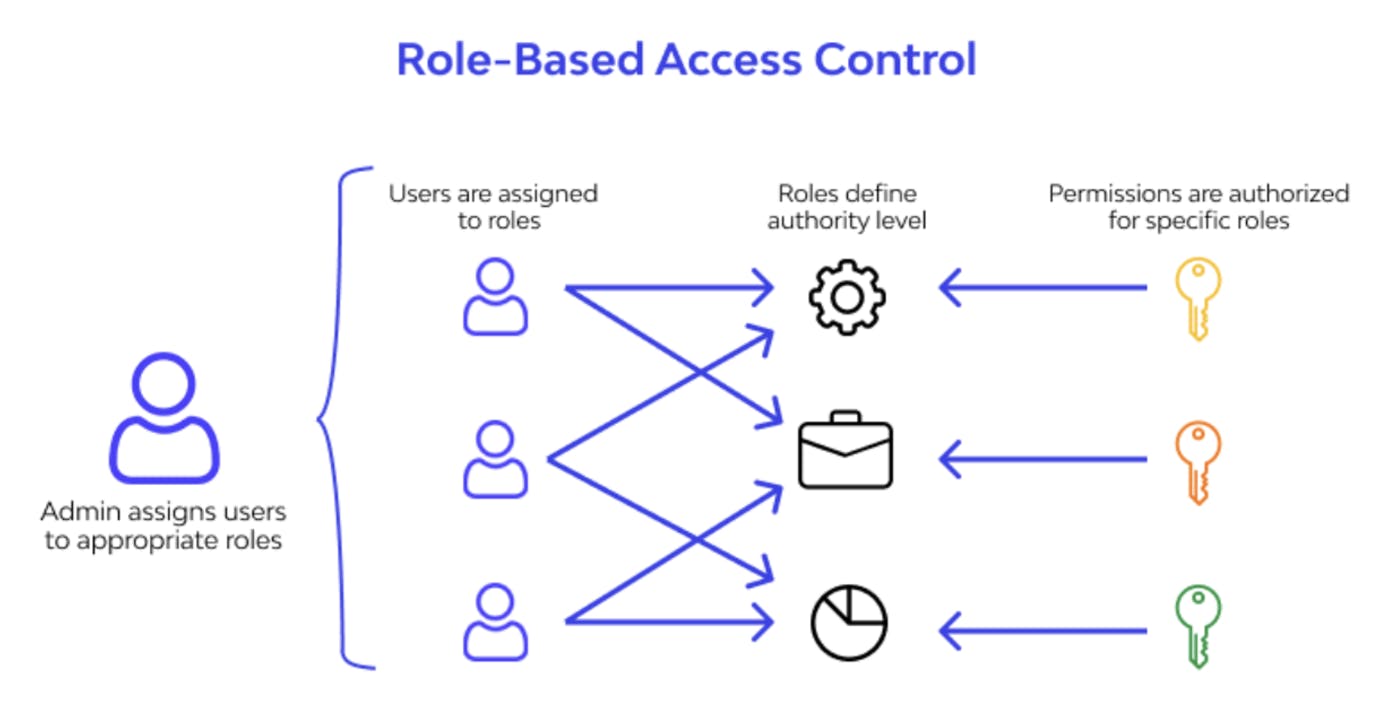
Image credits: wallarm
When you arrive at the office entrance (authentication), you provide your ID to confirm your identity. Once verified, RBAC takes over. It's like a personalized guide that directs you only to the floors and rooms you're authorized to enter based on your role and responsibilities.
For instance, if you're in the finance department, you'll have access to financial records on Level 5, but you won't be able to enter the research and development area on Level 3. RBAC ensures that every employee can perform their tasks smoothly within their designated areas but prevents them from wandering into spaces where they don't belong.
Without RBAC, chaos could ensue. Employees might accidentally stumble into restricted zones, potentially exposing sensitive information or disrupting workflows. RBAC, represented by a set of rules, acts like the invisible hand guiding employees through the office maze.
In this real-world scenario, RBAC is the behind-the-scenes hero, making sure everyone can navigate the office seamlessly while maintaining the security and confidentiality needed for a smooth work environment. It's the tool that empowers employees to access what they need and safeguards against unauthorized entry into sensitive spaces.
Challenges in Multi-cluster RBAC Management:
Like any piece of technology, RBAC has its challenges as well. These challenges are even greater recognized once we start increasing scale. Whether it’s the scale of organizations, applications, or infrastructure. Let’s try and quickly understand some of these challenges.
Role Explosion:
A growing number of roles for various users and groups.
Administration becomes challenging due to an increasing complexity of privileges.
Complexity and Scalability:
Challenges in managing relationships between numerous roles and permissions.
The lack of native tools for synchronization hampers comprehension.
Lack of Holistic View:
Kubectl provides granular information but lacks a comprehensive overview.
Understanding how different roles are used across clusters becomes difficult.
Imperative Execution:
Manual execution of kubectl commands prone to errors.
Time-consuming updates without continuous synchronization.
A single solution to our access security problems?
Now that we’ve got a good understanding of some of the history of security and some of the modern paradigms and problems with them, let’s think about how we can start solving these problems.
Instead of building our solutions from scratch, why not try and leverage what someone else has already built? Surely that saves us the effort of learning the deep intricacies and implementing things ourselves. I’m going to specifically talk about Tremolo, the security company for everything related to access management.

Image Credits: TremoloSecurity website
Let’s go over a couple of their open-source tools, and try to understand what they do, and if they are going to be useful for you.
OPENUNISON
Whether your Kubernetes clusters are running the cloud, on-prem, or in a hybrid mode, OpenUnision is a project that can provide robust authentication and SSO functionalities to your Kubernetes clusters. It also incorporates a zero-trust mode right out of the box, so you don’t have to worry about your cluster keys falling into the wrong hands.
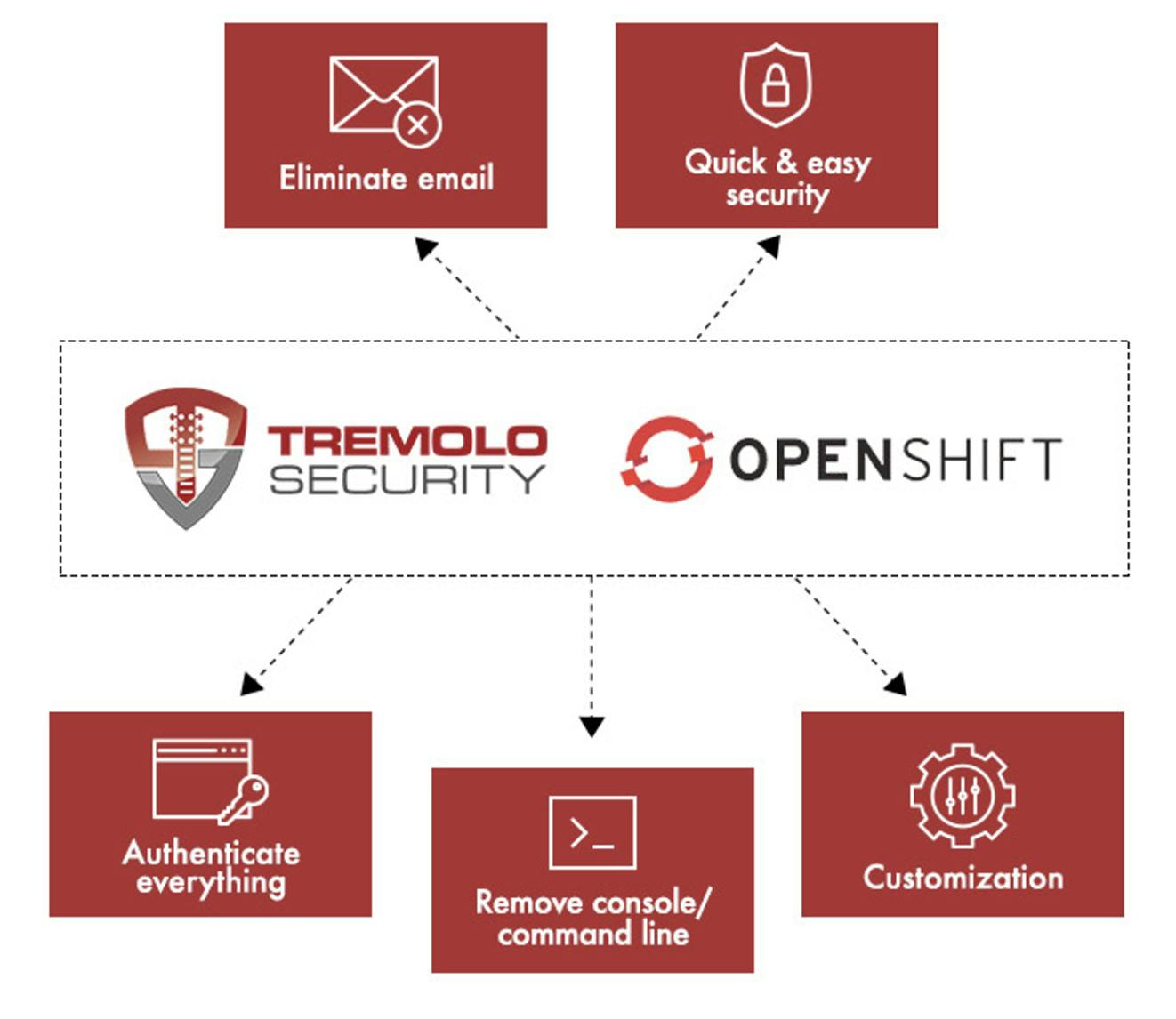
Image Credits: Tremolo Security Website
OpenUnison combines the identity services that are most used by applications into a single system that is quick to deploy, easy to use, and simple to maintain. The identity services provided by OpenUnison include:
Authentication - Who are you? How do we know that?
Session Management - How did you log in? What do you have access to?
Identity Federation - SSO across domains
User Provisioning - Creating and managing identity data in systems and applications
Access Request Management - Why do you have access?
MyVirtualDirectory
A virtual directory is a service (typically provied via LDAP) that allows for the integration of multiple data repositories in a transparent manner to an application. There are several use cases for a virtual directory including (but not limmited to):
Creating a view of a user with attributes stored in multiple repositories
Formatting user and group object for an application
Creating a larger directory from smaller ones
To learn how a virtual directory can help integrate your applications with your identity data view some virtual directory use cases.
Image Credits: TremoloSecurity GitHub page
Virtual Directories have several use cases. In general a virtual directory is most easily used to help integrate an application into an existing environment. Each of the below usecases is examined in more detail with a description of how MyVirtualDirectory might solve the given problem.
Namespace Integration - Integrating multiple directories to form a larger single directory
Delegated Authentication - Delegating authentication to an enterprise directory while using an edge directory for identity data
Data Transformation - Transform existing directory data for use by an application
Edge Directory Integration - Integrate application specific directory data into an enterprise directory without making any changes to the enterprise directory.
Web Services Integration - Many organizations have web services for the creation and update of user information
Conclusion
As businesses venture into the realm of cloud-native environments, the complexities of securing access to digital assets have evolved significantly. Traditional security models, anchored in physical fortifications and network perimeters, have given way to dynamic paradigms like Zero Trust Security, Single Sign-On (SSO), Identity and Access Management (IAM), and Role-Based Access Control (RBAC).
In response to these transformations, Tremolo Security has created many tools that act as harmonious solutions, orchestrating self-service identity management and unifying identity data seamlessly. These tools collectively address the challenges posed by the distributed nature of modern networks and Kubernetes environments.
From the granular control of Zero Trust Security to the streamlined user experiences enabled by SSO, IAM's robust access controls, and RBAC's effective permission management, Tremolo Security's suite provides a comprehensive melody for securing cloud-native ecosystems. The benefits span enhanced security postures, improved user experiences, and increased agility for organizations navigating the intricate landscape of digital transformation.
If you're interested in more check out this awesome Twitter Space with Marc, CTO @ Tremolo Security, Marino, Kat, and Aakansha: https://twitter.com/i/spaces/1yoKMwOEMbWJQ
And if you want to see some of this in action, check out this video of OpenUnison in action, and feel free to follow the docs via GitHub!
Finally, we look forward to seeing you in the next Twitter/X-Space on Tuesday @ 10AM ET !!!
Thank you for reading :)!!!
